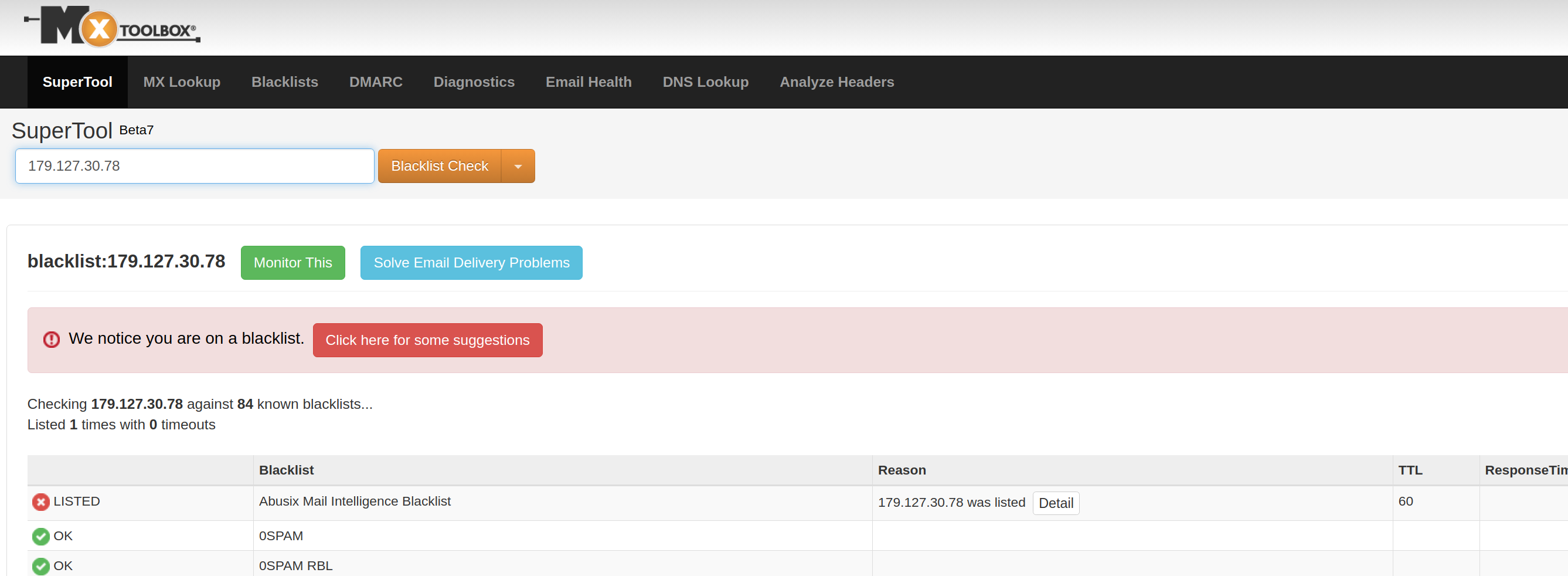
Blocked on SPFBL by spammers
The SPFBL is a remote blacklist designed to store information about known spammers and distribute this information to their customers via DNS.
Interestingly, it appears that spammers are also using SPFBL against legitimate mail servers.
In our case, spammers operating from vinhedo.nuvemidc.com (client=vinhedo.nuvemidc.com[179.127.30.78]) attempted to send us spam email from the address contato@goomarketing.com.br.
Some investigation:
$ dig MX goomarketing.com.br +short
0 _dc-mx.910d187fe7de.goomarketing.com.br.
$ dig _dc-mx.910d187fe7de.goomarketing.com.br. +short
179.127.30.78
$ dig -x 179.127.30.78 +short
vinhedo.nuvemidc.com.
Ansible module Debug
The ansible module debug outputs contents of variables.
For insance here a variable associated with a specific host:
- name: Show all variables/facts known for a host
debug:
var: hostvars['myserver.example.com']
verbosity: 1 # default verbosity is 0, max verbosity is 4
So it displays:
- Facts they gathered about the host: all things Ansible gathers about the host. Things like IP addresses, disk space etc.
- Facts from host vars and group vars: if we have variables defined for the specified host in host_vars or group_vars, they are displayed too.
- Facts defined in the role: for example in defaults/main.yaml
- All other variables that set during the execution of the playbook: variables for the playbook, variables specified on the commandline or facts registered during the exectution of the playbook.
Example how to specify a variable on the command line:
Dmesg Notes
Log levels
To set current log level, run dmesg --console-level loglevel
For intance:
dmesg --console-level debug
The log level can be checked in /proc/sys/kernel/printk
# cat /proc/sys/kernel/printk
8 4 1 7
The first of the numbers is the one we’ve just set and 8 means debug.
Here are meanings of these numbers, but for me, only the first and last are interesting:
| Number | Description |
|---|---|
| 8 | current console log level |
| 4 | default message log level for messages without a specific log level. |
| 1 | minimum log level |
| 7 | boot-time-default log boot-time-default log level (used during initial stages of the boot process) |
The log levels with their numbers as displayed in /proc/sys/kernel/printk:
iDrac 9 issue LC023: Cannot access network share
I have a new server and tried to update it from downloads.dell.com via iDRAC, but it kept failing.
LC023: Cannot access network share. Check network share access credentials (IP address, user name, password, share type, and so on). Refer to your product documentation for more details.
TLDR
This error can by caused by all sorts of network issues, but in my case it was caused by a problem with DNS. As soon as I configured a functional DNS resolver (Google’s 2001:4860:4860::8888), the update started working.
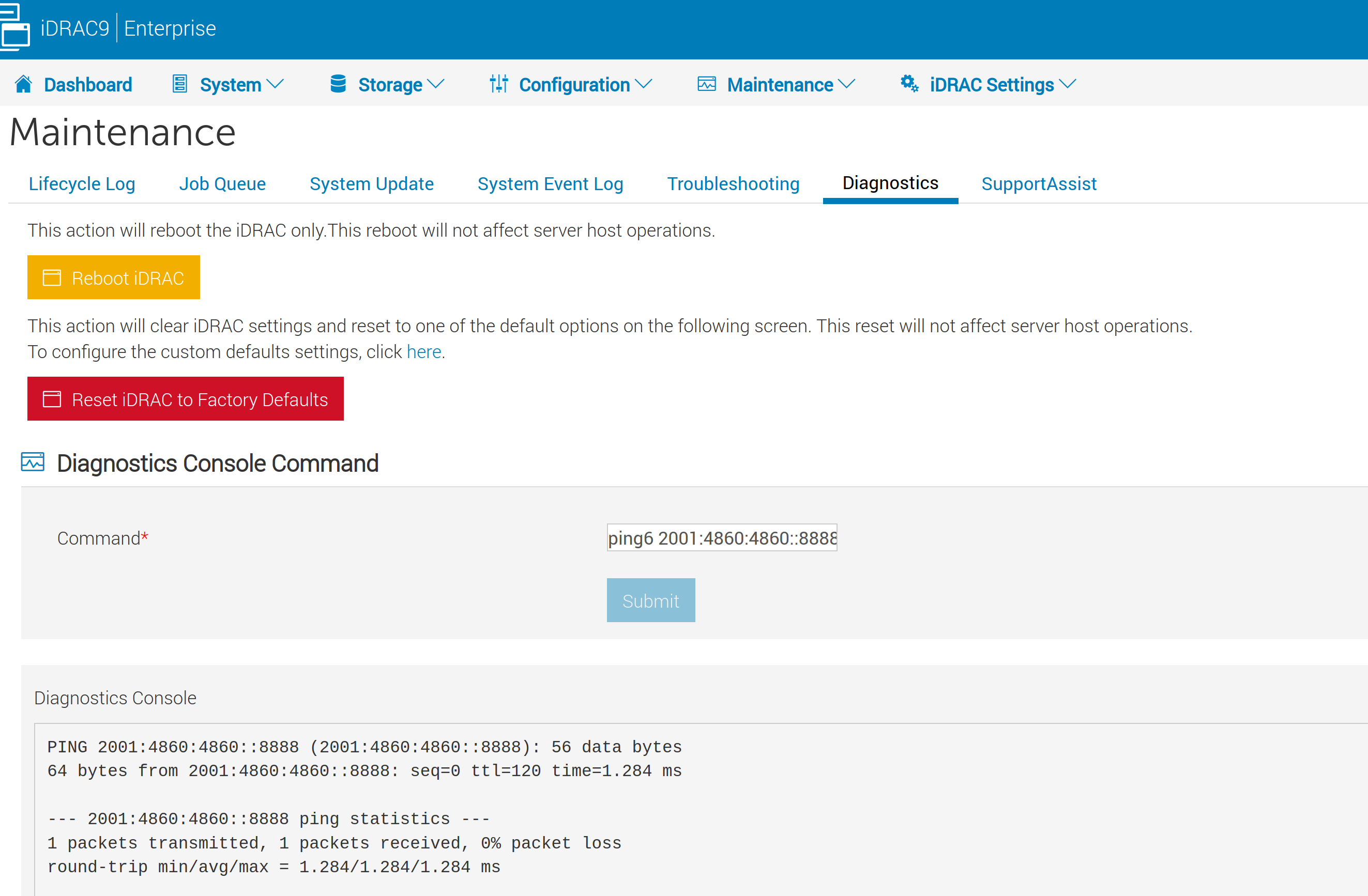
Idrac 9 Diagnostics
Web interface of iDrac tend to confuse me so this time I decided to note where to find to option to run diagnostic commands in iDrac.
I have these options in the dropdown menu in the top part of the window:
Dashboard » System » Storage » Configuration » Maintenance » iDrac Settings
The option to enter the Diagnostics Console Command is under the Maintenance and diagnostics.
Ansible and User Accounts
From time to time, I get confused when it comes to Ansible and things like default_user, become, become_method and become_user. To make my life easier the next time, I prepared this note.
default_user
If we specify no user at all, Ansible will use the user that is running the ansible-playbook command.
For instance if I run ansible-playbook as user jirka, it’s going to try logging in as jirka to the remote machine. Of course this will succeed only if the account with the same name exists on the remote machine and if I either provide remote user’s password or the remote account jirka has public key of that account in authorized keys (/home/jirka/.ssh/authorized_keys).
Ubuntu - full /boot - Write Error
The /boot directory on my Ubuntu got filled and because of that, updates started failing.
I expected Ubuntu to take care of space in the /boot directory. After all, I let Ubuntu to choose the size of /boot when I was installing it and it’s Ubuntu who choses how long to keep old kernels in the /boot.
It would be possible to create /boot bigger during the installation or to enlarge it later, but I prefer to keep my instalations as standard as possible and to treat them more like cattle rather than pets, so I am going to keep making space whenever I run into this problem in the future and I am creating this note to meake it easier next the time.
Youtube chanell rwxrob
I really like videos from youtube chanel rwxrob by Rob Muhlestein. It seems that Youtube keeps hiding his videos from me so I making this note to be able to find them easily whenever I want.
And this is also a good place where to keep other links related to Rob:
My favorite Rob’s videos so far are these:
Why shell scripts over plugins in Vim
What do you thing of Vim9’s new Vimscript
What app do you use to take notes?
My Window Manager is TMUX
Screen, TMUX, Multi-wha?
Emails: Useful Links and Tools
MXToolbox - MX, DKIM, DMARC, mailserver test etc.
Kitterman - SPF Validation
Workaround - An exceptionally good guide for installation of a mail server.
CheckTLS - test SMTP SSL
Ansible - problem with adding Postgresql user
Today I strugled a bit with adding a PostgreSQL user using Ansible. The fault was on my side so I am making this note to avoid it in the future.
The task looked like this:
- name: Create PostgreSQL user
become: yes
become_user: postgres
postgresql_user:
name: mynewuser
password: 'mystrongpassword'
encrypted: yes
login_host: localhost
login_user: postgres
The user postgres was created during the installation of the Postresql and Ansible was supposed to use it to create a new account, here called “mynewuser”.